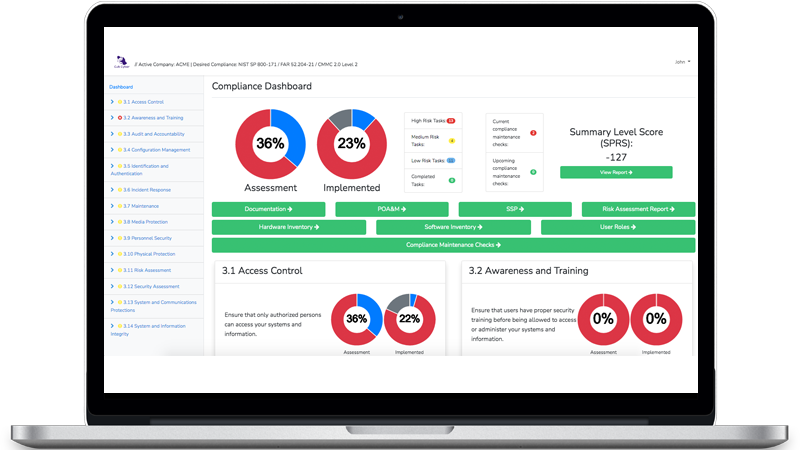
Requirement
1-1-1 – A cybersecurity strategy must be defined, documented and approved. It must be supported by the head of the organization or his/her delegate (referred to in this document as Authorizing Official). The strategy goals must be in-line with related laws and regulations.
This control comes from Essential Cybersecurity Controls (ECC – 2 : 2024).
Understanding the Requirement
This control requires your business to create a formal cybersecurity strategy that is written down, clearly aligned to your organization’s goals and legal obligations, and formally approved by your top executive (the Authorizing Official) or their delegate. In practice, it means deciding where you need to go with cybersecurity, documenting how you will get there, and ensuring leadership takes ownership of the plan.
Policies and Procedures Needed
SMBs should establish a Cybersecurity Strategy and Governance Policy that defines ownership, approval authority, and review cadence; a documented Authority Matrix identifying who can approve the strategy; a Regulatory and Legal Mapping Procedure to align goals with applicable laws; a Strategic Planning Procedure to run stakeholder workshops and set objectives; and a Document Control Procedure for versioning, communication, and periodic review. Together, these policies ensure the strategy is created, approved, compliant, and actively maintained.
Technical Implementation
- Confirm the Authorizing Official (e.g., CEO, Managing Director) and publish an authority matrix. Define roles and a RACI for drafting, reviewing, approving, and maintaining the strategy. Store the matrix in a controlled location (e.g., SharePoint, GRC tool) and reference it in the policy.
- Run a stakeholder workshop (IT, security, risk, legal/compliance, HR, finance, operations) to align cybersecurity objectives with business objectives. Capture minutes, risks, priorities, and budget constraints. Turn outputs into 3–6 clear strategic objectives.
- Draft a Cybersecurity Strategy document that includes: Vision, Mission, Strategic Objectives, Strategy Implementation Plan, Projects, and Initiatives. For each objective, define success metrics (KPIs), owners, timelines, and dependencies. Map each objective to applicable laws and regulations (e.g., national cyber or privacy requirements, sector rules, or local codes such as CCC/CSCC where relevant).
- Create a simple regulatory/obligation register: list each applicable regulation or contract clause, note the related strategy objective(s), and identify evidence you will produce. Validate with legal or compliance advisors and keep it version-controlled.
- Establish an approval workflow: internal review by IT/security and risk/compliance, then formal approval by the Authorizing Official per the authority matrix. Use electronic signatures, record version, date, approver, and next review date. Publish a read-only PDF and communicate it to all stakeholders.
- Operationalize the strategy: translate objectives into a 12–24 month roadmap with projects and initiatives, estimated budgets, owners, and quarterly milestones. Report progress to leadership quarterly; adjust based on threats, audits, or business changes. Schedule an annual strategy review or an ad-hoc review when major changes occur (e.g., merger, new regulation).
Example in a Small or Medium Business
Acme Components, a 180-employee manufacturer, appoints the CEO as the Authorizing Official and publishes a simple authority matrix naming the IT Manager as the strategy drafter and the CFO as compliance reviewer. The IT Manager convenes a two-hour workshop with operations, HR, finance, and sales to align business goals (on-time delivery, new B2B portal, export growth) with cyber objectives. The team drafts a strategy with a short vision and mission, four objectives (protect production systems, secure the B2B portal, meet customer compliance obligations, and improve incident readiness), and an 18-month implementation plan. Each objective has KPIs (e.g., patch SLA > 95%, MFA adoption > 98%), owners, and budgets. They map objectives to applicable laws and contract clauses from key customers, noting evidence such as policies, system configs, and audit logs. After internal review, the CEO formally approves the strategy via e-signature; the PDF and approval record are stored in SharePoint with a one-year review date. The roadmap is entered into a simple tracker, and a quarterly steering meeting reviews progress, risks, and funding needs.
Summary
Meeting 1-1-1 means building a leadership-backed, documented cybersecurity strategy that aligns with your business goals and legal requirements, and then turning it into an actionable plan. With the right policies (governance, authority, legal mapping, document control) and concrete steps (stakeholder alignment, clear objectives, measurable KPIs, mapped obligations, formal approval, and routine review), an SMB can demonstrate intent, direction, and accountability. Regular reporting and updates ensure the strategy remains relevant as the business and threat landscape evolve.